
The Hidden Drawbacks of Wi-Fi: What You Need to Know
Uncover the hidden drawbacks of Wi-Fi that could be affecting your connectivity and security. From potential interference issues to security vulnerabilities, understanding these disadvantages is[…]

Maximize Efficiency: Third-Party Subscription Solutions
Unlock the full potential of your subscription services by leveraging third-party solutions for content delivery and payment processing. Streamline operations, enhance user experience, and boost[…]

The Importance of Hi-Res Files in Digital Projects
Exploring the impact of high‑resolution file delivery

Mastering VoIP: The Essential Guide to SIP and RTP
Exploring how modern VOIP standards enhance communication

The Impact of 3G Technology on Global Communication
Exploring how 3G shaped global connectivity and growth

Optimize Nontext Files for Better Web Performance
Ensure your files use correct types for better access

Master TypeScript: A Beginner’s Guide to Understanding Basics
Learn how TypeScript simplifies coding with real cases

Maximizing Wi-Fi 5 Indoor Range: Tips and Insights
Exploring WiFi 5 range, performance, and real use cases

Understanding Wi-Fi: The Key to Seamless Connectivity
Exploring how Wi-Fi connects technology to daily life

Understanding Wireless Communication Systems: Key Components
Exploring what powers modern wireless connections

The 802.11b Standard and Its 2.4GHz Frequency Impact
Exploring how 802.11b frequency improves Wi-Fi use
Mastering C++: A Beginner’s Guide to Programming Basics
Learn C++ essentials through examples and real cases

How HTML Structure Enhances SEO Performance
A well-structured HTML code is crucial for enhancing website visibility and user experience. Semantic coding improves SEO by allowing search engines to accurately index content.[…]

A Guide to Mesh Networks: Benefits and Uses
Mesh networks, also known as wireless mesh or self-healing systems, connect multiple nodes to enhance reliability and coverage, making them ideal for homes and businesses.[…]

How to Estimate Your Website Traffic Effectively
Estimating website traffic is crucial for success, as it affects user experience, conversion rates, and server stability. Accurate projections rely on data analysis, understanding business[…]

Understanding Wireless Network Security Goals
Wireless networks are essential for connectivity, requiring a robust security strategy focused on three core goals: Confidentiality, Integrity, and Availability (CIA). Organizations often overlook structured[…]

Why Payment Flexibility Matters for Online Sales
In today’s digital environment, businesses must provide various payment options to enhance user experience and reduce cart abandonment rates. Key methods include credit cards, digital[…]
SATA vs SSD: Which Storage Technology is Right for You?
Choosing between SATA and SSD storage impacts system performance significantly, affecting boot times and application responsiveness. SATA, while cost-effective for bulk storage, has slower speeds[…]
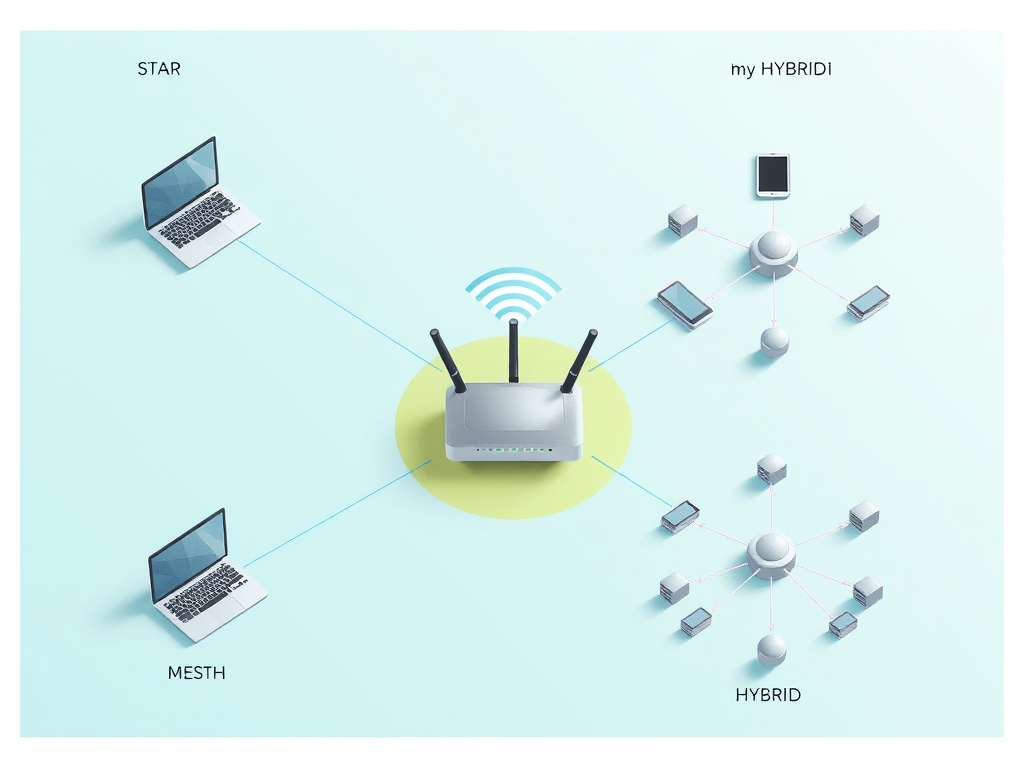
WiFi Network Topologies Explained: Star, Mesh, and Hybrid
WiFi network topology, the structural arrangement of devices like routers and access points, is vital for efficient connectivity in personal and professional environments. Key types[…]
Understanding 1024-QAM vs 256-QAM Modulation
The article examines the differences between 1024-QAM and 256-QAM modulation techniques, highlighting their impact on data transmission efficiency, capacity, and performance in various environments. While[…]

Why WEP is No Longer Secure: Understanding Its Vulnerabilities
Exposing the weaknesses and real risks of WEP security

Can MAC Filtering Secure Your Wi-Fi Network?
Wireless networks are essential in modern life, but securing them remains a challenge. MAC filtering can help manage device access through a whitelist of unique[…]

Discover How WI-FI Empowers and Supports Communities
Discover the transformative power of WI-FI in bridging communities and fostering growth. By providing essential connectivity, WI-FI empowers individuals with access to education, healthcare, and[…]

