
Understanding the Function and Purpose of a Modem
Discover how modems connect you to the digital world

Understanding Very Low Frequency Transmission Waves
Exploring wavelength and uses of very low frequency waves

Understanding the Function of the Session Layer
How the session layer manages connections and data flow

Best Website Styles for a Professional Financial Analyst
Design insights for engaging financial analyst websites

Scaling Made Simple How to Adjust Plans as Traffic Grows
Easily scale hosting plans as your website traffic grows

Understanding the Difference Between Download and Upload
Learn how download and upload speeds impact performance

How to Create a Secure and Reliable Guest Network
Keep your guests online safely with a secure network

How AI Is Revolutionizing Hosting Management Today
AI transforms hosting with smarter, faster management

Understanding How WiMAX Uses Standard Specifications
Exploring how WiMAX follows global standards effectively

Understanding the Standard Form of the U NII Band
Exploring how U-NII bands define reliable wireless links

Understanding ISM and UNII Frequency Band Licensing
Exploring licensed and unlicensed wireless frequency bands

Do You Really Own the Rights to Your Digital Files
Understanding your real ownership of digital files

Exploring What Content Belongs Behind Password Walls
Securing premium insights and exclusive digital access

Understanding the Different Types of Wireless Networks
Exploring types of wireless networks and their roles

Exploring the Many Ways to Configure a Wireless LAN
Discover flexible methods to set up your wireless LAN

Understanding WP CLI and Why It Matters for You
Boost your WordPress workflow with powerful WP-CLI tools
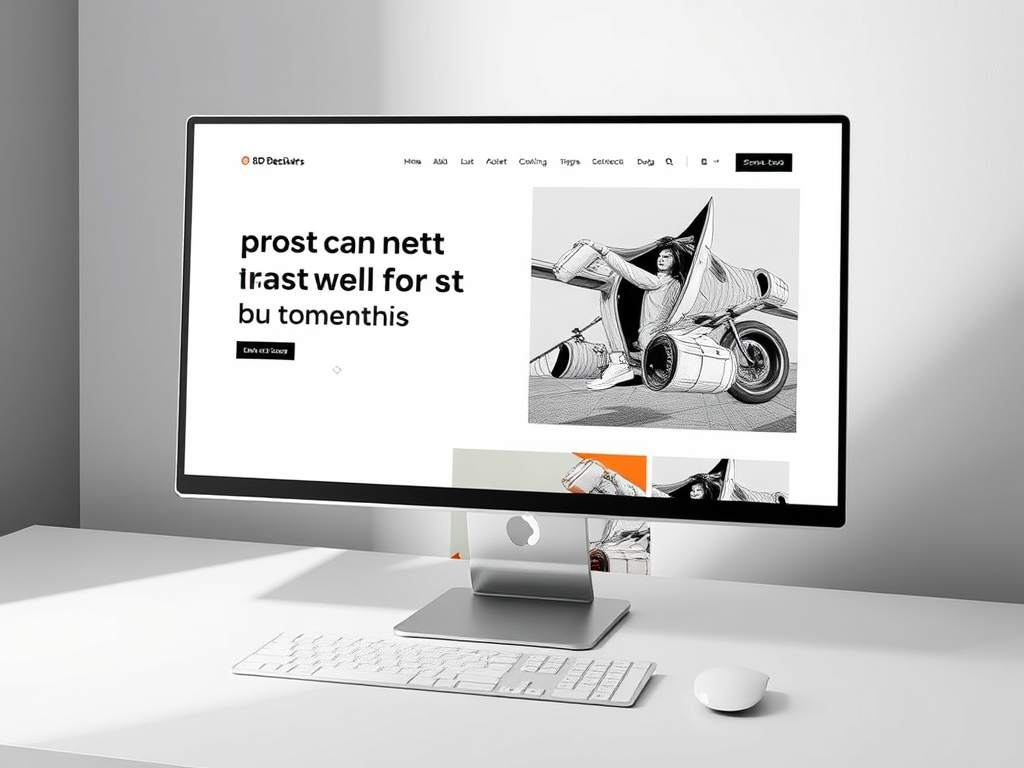
Best Website Design Ideas for Graphic Designers
Design a site that reflects creativity and guides users

Understanding WiFi Performance and User Experience
Improving WiFi usability through design and clarity

Key Benefits of Having an FTP Account for Websites
Boost your site’s efficiency with secure FTP access





